Reverse Engineering with DOSBox debug build
DosBox comes with it's own built-in debugger, which can be useful when reversing old DOS games.
This feature needs to be enabled at build time (--enable-debug or --enable-debug=heavy), so either download the special binary or build it from source. I went through the build process in a previous post: https://blog.aupcgroup.com/index.php?/archives/32-Hacking-a-DOS-32-bit-protected-mode-game-from-1997.html
This gives a nice view with registers, dissassembly and memory views:
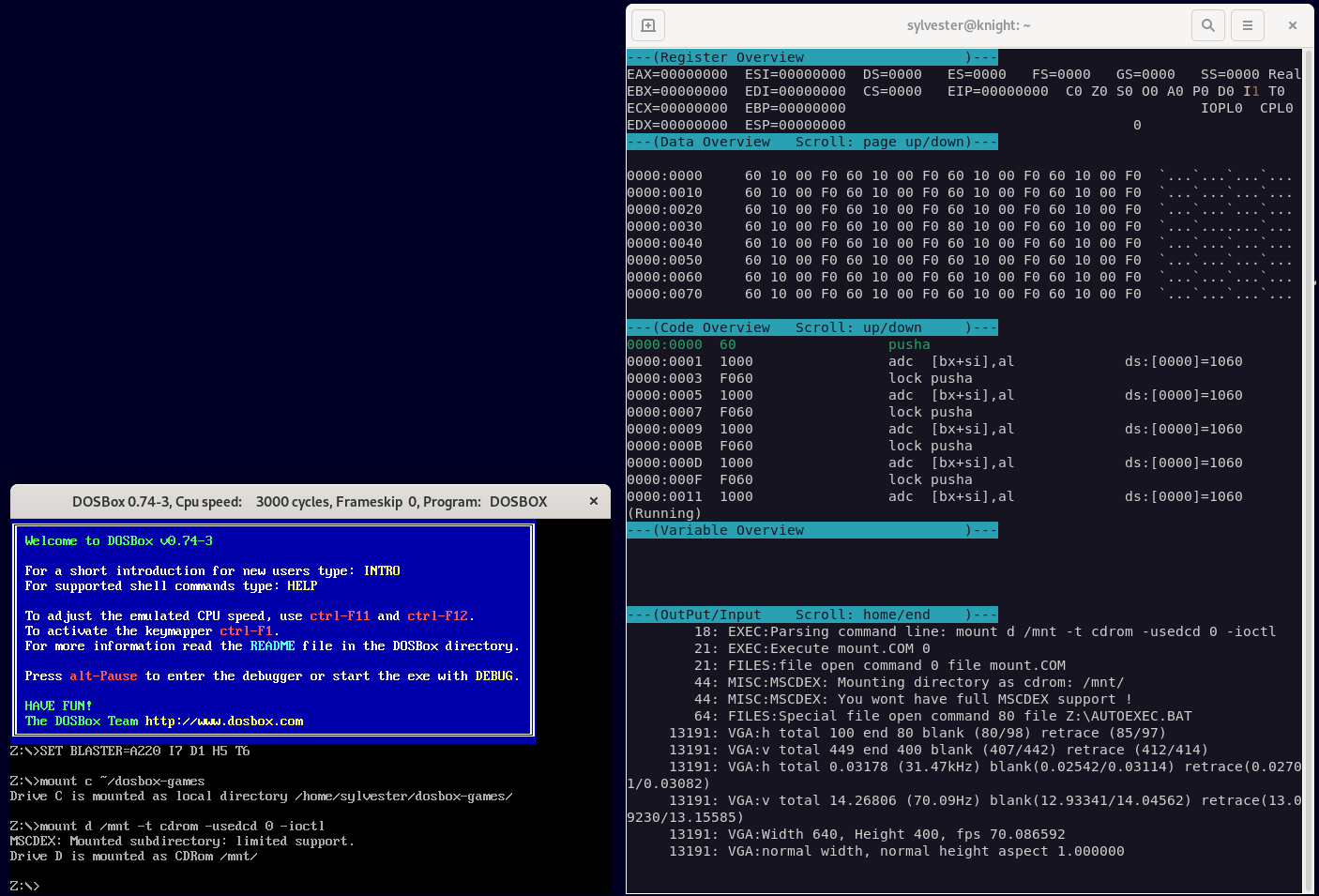
This VOGONS thread has a quick summary on the DosBox built-in debugger: https://www.vogons.org/viewtopic.php?t=3944
Continue reading "Reverse Engineering with DOSBox debug build"